Attempt time: 340 mins
Flag: N/a
So, I didn't actually solve this challenge. I ended up taking a look at writeups, I got stuck trying to brute force a crc32 check. Overall, I learned a ton from this challenge and I don't view it as a failure even though I didn't solve it. It was definitely a learning experience.
The challenge began with a tar file called Antioch.tar. Once I unpacked the tar file, I realized it was a docker container. Eventually I realized I could just load the docker container using the docker load --input antioch.tar command. Once I ran the docker container there was a prompt of:
AntiochOS, version 1.32 (build 1975)Type help for help>
It wasn't clear what commands I could run. By inspecting the binary I identified the following commands:
The approach command prompted me for my name. The consult command just printed a ton of VVVs and then prompted for another command again. What felt like a good place to start was understanding how the name check was working.

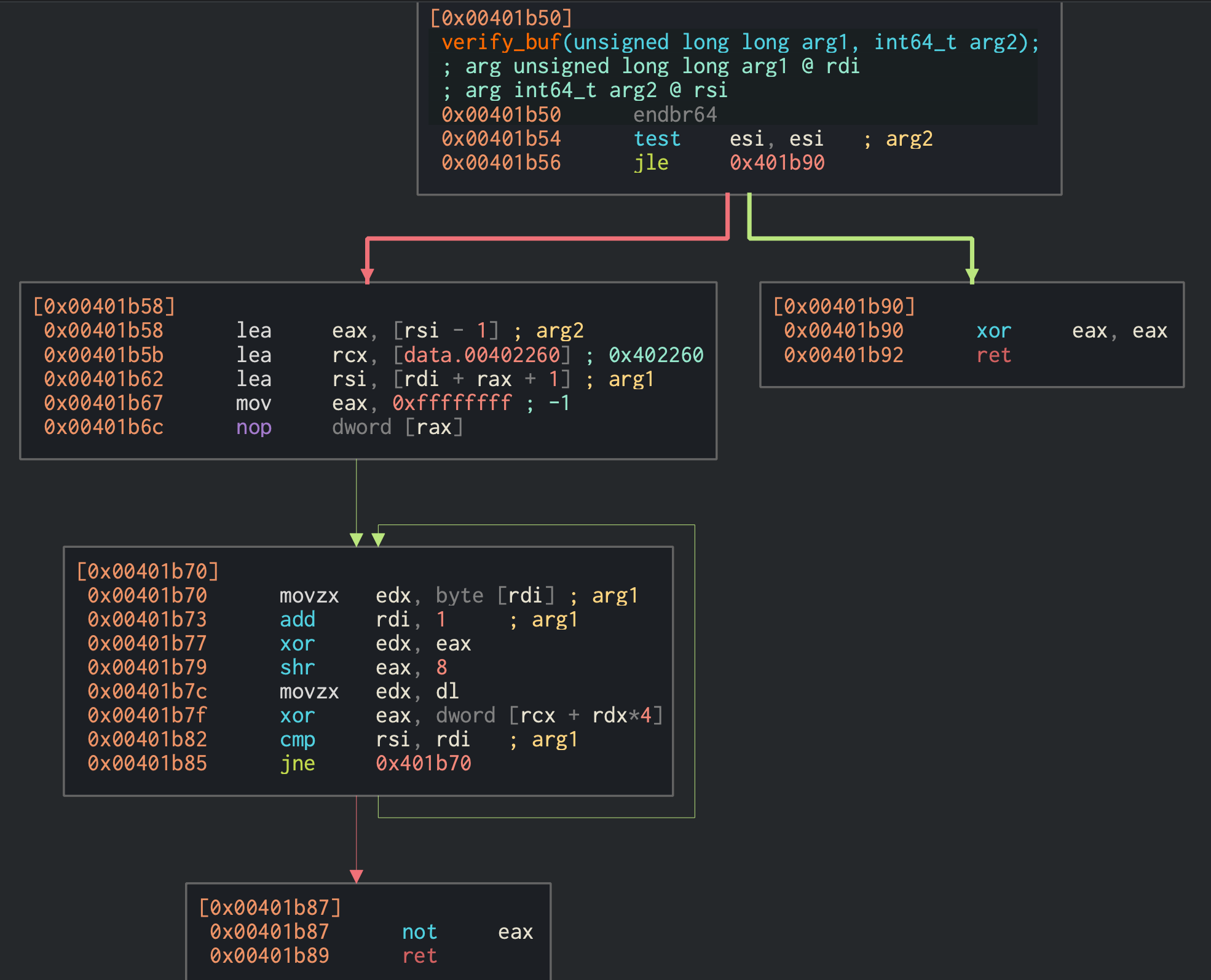
Above is the disassembly. After reading some write-ups, I now know that this is a crc32 hash function. Not having a clear way to reverse the function. I simply implemented it in python and then brute forced it with the names I found in the docker layers. Each docker layer had an author with a Monty Python character associated with it. I was successfully able to find the hash of Bridge Keeper. I failed to realize that all of the Monty Python names were valid. I also got stuck on brute forcing the correct color for each name.
The steps after where I got stuck was
consult command with the correctly ordered layersI suggest 0xdf's writeup if you want more details!